outsmart cybercriminals
OVERVIEW
Why Choose a Career as an Ethical Hacker?
- Make a Real Impact: Strengthen systems and prevent attacks as a Penetration Tester, Ethical Hacker, or Security Consultant, safeguarding businesses and users.
- High Demand: Ethical hacking skills are sought after by tech firms, governments, and corporations, offering diverse opportunities in a critical field.
What Does an Ethical Hacker Do?
As an Ethical Hacker, you’ll:
- Conduct penetration tests to identify weaknesses in networks, applications, and systems.
- Simulate cyberattacks to uncover vulnerabilities before criminals do.
- Recommend fixes and collaborate with teams to improve security.
Average Ethical Hacker Salary in South Africa
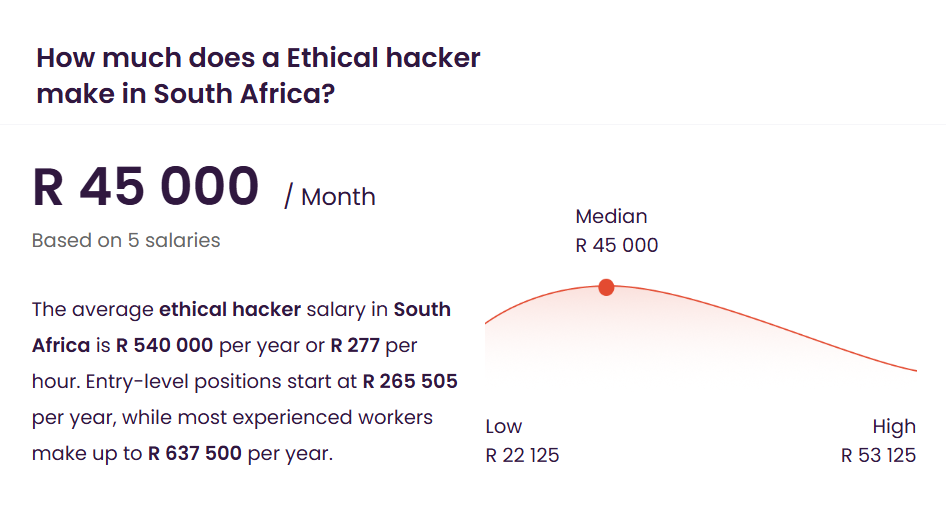
Source: Talent.com

Grade 12 with foundational knowledge in networking or cybersecurity. Prior experience is highly beneficial.
- Penetration Tester,
- Ethical Hacker
- Security Consultant
- Vulnerability Analyst
Duration: 18 Months
Delivery Mode Mode: Online Self Paced
R80 500.00
Duration: 18 Months
Total Fees: R80 500.00
Deposit: R5 000.00
Balance After Deposit: R75 500.00
Monthly Installment (12 Months): R6 292.00
CERTIFICATIONS
EXAM CODE N10-008 & N10-009
CompTIA Network+ validates the core skills necessary to establish, maintain, troubleshoot and secure networks in any environment, preparing you for a rewarding career in networking and cybersecurity.
What Skills Will You Learn?
- Networking Concepts
Explain basic networking concepts, including the OSI model, network appliances, applications, cloud concepts, connectivity options and more. - Network Implementations
Understand routing technologies and important factors of physical installations; configure switching technologies and wireless devices. - Network Operations
Monitor and optimize networks to ensure business continuity. - Network Security
Understand security concepts and network attacks to harden networks against threats. - Network Troubleshooting
Explain the troubleshooting methodology and address common issues related to networking, including cable, connectivity, and software problems.
EXAM CODE SY0-701
CompTIA Security+ is a global certification that validates the baseline skills necessary to perform core security functions and pursue an IT security career.
What Skills Will You Learn?
- General Security Concepts
Establish a strong foundation in cybersecurity by learning key terminology and core concepts that support understanding of security controls and practices throughout the course. - Threats, Vulnerabilities & Mitigations
Learn how to identify and respond to common threats, cyberattacks, vulnerabilities, and security incidents. Apply effective mitigation techniques to monitor and secure hybrid environments. - Security Architecture
Understand the security implications of various architecture models. Learn the principles of securing enterprise infrastructure and strategies to protect sensitive data. - Security Operations
Enhance your skills in security and vulnerability management. Gain insight into the security impact of managing hardware, software, and data effectively. - Security Program Management & Oversight
Develop reporting and communication skills essential for roles in governance, risk management, compliance, assessments, and security awareness. Align with modern Security+ job role expectations.
EXAM CODES PT0-002 & PT0-003
CompTIA PenTest+ is for cybersecurity professionals tasked with penetration testing and security consulting.
What Skills Will You Learn?
- Engagement Management
Master techniques for effective engagement planning, including scoping, understanding organizational and customer requirements, and applying governance, risk, and compliance principles. Enhance skills in reporting, communication, and remediation recommendations, all while adopting an ethical hacking mindset. - Reconnaissance and Enumeration
Develop advanced skills in passive and active information gathering. Learn to perform enumeration and conduct system inventories, including identifying scripting types and understanding their use cases—without requiring hands-on coding. - Vulnerability Discovery and Analysis
Gain expertise in using vulnerability scanning tools and performing detailed vulnerability analysis. Understand how to identify and address both digital and physical security weaknesses. - Attacks and Exploits
Learn how to analyze targets and choose the most effective method of attack. Execute network, wireless, application-based, and cloud attacks. Stay ahead of the curve by exploring AI-driven threats and scripting automation techniques. - Post-exploitation and Lateral Movement
Focus on post-compromise activities including maintaining access, moving laterally through systems, staging and data exfiltration. Learn best practices for clean-up and system restoration after engagement.
Validate your knowledge and skills in network fundamentals and access, IP connectivity, IP services, security fundamentals, and more. Take your IT career in any direction by earning a Cisco Certified Network Associate (CCNA) certification.
What You Will Learn:
- Networking Fundamentals
Master the basics of networking equipment, configurations, and troubleshooting techniques to ensure reliable network performance. - IP Services
Learn how to configure routing for various IP versions, understand redundancy protocols, and interpret routing tables. - Security Fundamentals
Gain foundational knowledge of cybersecurity, including threat identification and prevention, user awareness training, and secure access setup. - Automation
Explore how automation transforms network management. Learn to work with APIs and configuration tools, and understand the difference between traditional and controller-based networking.
Learn how to monitor, detect and respond to cyber threats and prepare for the Cisco Certified CyberOps Associate certification
What You Will Learn:
- Security Concepts
Understand core cybersecurity principles, threat classifications, and foundational defense mechanisms. - Threat Detection
Explore how to identify and classify different types of cyber threats using real-time monitoring tools. - Security Monitoring
Learn how SOC teams use tools to detect and investigate suspicious activity and ensure infrastructure security. - Incident Response
Master the techniques used to respond to security incidents and restore normal operations efficiently. - Network Intrusion Analysis
Analyze network traffic to identify unauthorized access and potential breaches. - Host-based Analysis
Use endpoint data and security tools to monitor and investigate potential host-based threats. - Attack Methods & Malware Analysis
Gain insights into various attack techniques and learn how malware operates within compromised systems. - Data and Event Analysis
Perform analysis of logs and security events to identify patterns, anomalies, and indicators of compromise. - Security Policy and Procedures
Understand the importance of policies and frameworks in maintaining organizational security posture. - Computer Forensics
Learn the fundamentals of digital forensics and evidence collection for investigations. - Cryptography
Explore how encryption and secure communications protect sensitive data. - SOC Metrics & Security Operations (SecOps)
Evaluate the performance of security tools and teams, and align with best practices in a SOC environment.
